IT-Mikrotik
Mikrotik Tutorial
Thursday, July 22, 2021
Monday, April 12, 2021
Load Sharing 2 WAN and Provide PPPoE Account, DHCP, SATIC IP for LAN by Using VLAN
Load Sharing 2 WAN and Provide PPPoE Account, DHCP, SATIC IP for LAN by Using VLAN
Monday, April 27, 2020
Bonding Configuration (Auto Protection)
Bonding Configuration (Auto Protection)
1. Create Bonding Interface
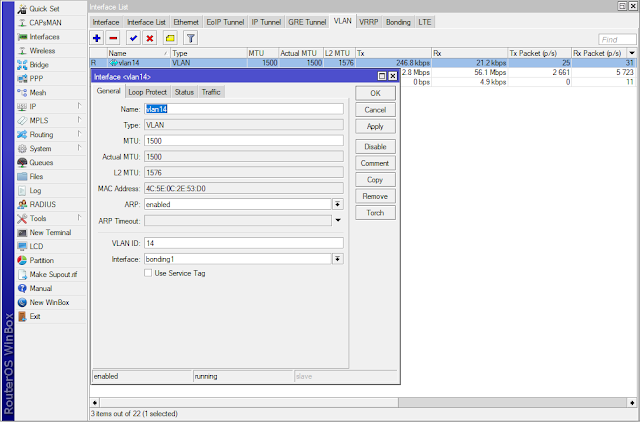
2. Create Vlan Management
3. Assign IP for Management Vlan
4. Add Static Route for IP Management
5. Create Bridge and Add Port to Bridge
In this configuration we use RouterBoard CCR1036-12G-4S with firmware 6.44.3
1. Create Bonding Interface
/interface bonding
add mode=active-backup name=bonding1 primary="sfp1--(ACTIVE)" slaves= "sfp1--(ACTIVE),sfp2--(BACKUP)" transmit-hash-policy=layer-2-and-3

2. Create Vlan Management
/interface vlan
add interface=bonding1 name=vlan14 vlan-id=14
add interface=bonding1 name=vlan102 vlan-id=102
add interface=bonding1 name=vlan896 vlan-id=896
3. Assign IP for Management Vlan
/ip address
add address=10.14.1.99/24 interface=vlan14 network=10.14.1.0
4. Add Static Route for IP Management
/ip route
add distance=1 gateway=10.14.1.1
5. Create Bridge and Add Port to Bridge
/interface bridge
add name=bridge-v102
add name=bridge-v896 protocol-mode=none
add bridge=bridge-v896 interface=vlan896
add bridge=bridge-v896 interface="ether2-Holiday Palace (Room L3-338)_21060"
1. Create Bonding Interface
2. Create Vlan Management
3. Assign IP for Management Vlan
4. Add Static Route for IP Management
5. Create Bridge and Add Port to Bridge
In this configuration we use RouterBoard CCR1036-12G-4S with firmware 6.44.3
1. Create Bonding Interface
/interface bonding
add mode=active-backup name=bonding1 primary="sfp1--(ACTIVE)" slaves= "sfp1--(ACTIVE),sfp2--(BACKUP)" transmit-hash-policy=layer-2-and-3

2. Create Vlan Management
/interface vlan
add interface=bonding1 name=vlan14 vlan-id=14
add interface=bonding1 name=vlan102 vlan-id=102
add interface=bonding1 name=vlan896 vlan-id=896
3. Assign IP for Management Vlan
/ip address
add address=10.14.1.99/24 interface=vlan14 network=10.14.1.0
4. Add Static Route for IP Management
/ip route
add distance=1 gateway=10.14.1.1
5. Create Bridge and Add Port to Bridge
/interface bridge
add name=bridge-v102
add name=bridge-v896 protocol-mode=none
/interface bridge port
add bridge=bridge-v102 interface=vlan102
add bridge=bridge-v102 interface="ether1-Holiday Palace (Room L1-88)_21059"
add bridge=bridge-v896 interface=vlan896
add bridge=bridge-v896 interface="ether2-Holiday Palace (Room L3-338)_21060"
Tuesday, January 28, 2020
Load Balancing 2 WAN with Hotspot
/ip firewall mangle
add chain=input in-interface=WAN1 action=mark-connection new-connection-mark=WAN1_conn
add chain=input in-interface=WAN2 action=mark-connection new-connection-mark=WAN2_conn
add chain=output connection-mark=WAN1_conn action=mark-routing new-routing-mark=to_WAN1
add chain=output connection-mark=WAN2_conn action=mark-routing new-routing-mark=to_WAN2
add chain=prerouting dst-address=192.168.1.0/24 action=accept in-interface=wlan2
add chain=prerouting dst-address=192.168.2.0/24 action=accept in-interface=wlan2
add chain=prerouting dst-address-type=!local in-interface=wlan2 per-connection-classifier=both-addresses-and-ports:2/0 action=mark-connection new-connection-mark=WAN1_conn passthrough=yes
add chain=prerouting dst-address-type=!local in-interface=wlan2 per-connection-classifier=both-addresses-and-ports:2/1 action=mark-connection new-connection-mark=WAN2_conn passthrough=yes
add chain=prerouting connection-mark=WAN1_conn in-interface=wlan2 action=mark-routing new-routing-mark=to_WAN1
add chain=prerouting connection-mark=WAN2_conn in-interface=wlan2 action=mark-routing new-routing-mark=to_WAN2
/ip route
add dst-address=0.0.0.0/0 gateway=192.168.1.100 routing-mark=to_WAN1 check-gateway=ping
add dst-address=0.0.0.0/0 gateway=192.168.2.100 routing-mark=to_WAN2 check-gateway=ping
add dst-address=0.0.0.0/0 gateway=192.168.1.100 distance=1 check-gateway=ping
add dst-address=0.0.0.0/0 gateway=192.168.2.100 distance=2 check-gateway=ping
/ip firewall nat
add chain=srcnat out-interface=WAN1 action=masquerade
add chain=srcnat out-interface=WAN2 action=masquerade
*PCC WITH HOTSPOT (Reference)
/ip firewall nat add action=accept chain=pre-hotspot disabled=no dst-address-type=!local hotspot=auth
add chain=input in-interface=WAN1 action=mark-connection new-connection-mark=WAN1_conn
add chain=input in-interface=WAN2 action=mark-connection new-connection-mark=WAN2_conn
add chain=output connection-mark=WAN1_conn action=mark-routing new-routing-mark=to_WAN1
add chain=output connection-mark=WAN2_conn action=mark-routing new-routing-mark=to_WAN2
add chain=prerouting dst-address=192.168.1.0/24 action=accept in-interface=wlan2
add chain=prerouting dst-address=192.168.2.0/24 action=accept in-interface=wlan2
add chain=prerouting dst-address-type=!local in-interface=wlan2 per-connection-classifier=both-addresses-and-ports:2/0 action=mark-connection new-connection-mark=WAN1_conn passthrough=yes
add chain=prerouting dst-address-type=!local in-interface=wlan2 per-connection-classifier=both-addresses-and-ports:2/1 action=mark-connection new-connection-mark=WAN2_conn passthrough=yes
add chain=prerouting connection-mark=WAN1_conn in-interface=wlan2 action=mark-routing new-routing-mark=to_WAN1
add chain=prerouting connection-mark=WAN2_conn in-interface=wlan2 action=mark-routing new-routing-mark=to_WAN2
/ip route
add dst-address=0.0.0.0/0 gateway=192.168.1.100 routing-mark=to_WAN1 check-gateway=ping
add dst-address=0.0.0.0/0 gateway=192.168.2.100 routing-mark=to_WAN2 check-gateway=ping
add dst-address=0.0.0.0/0 gateway=192.168.1.100 distance=1 check-gateway=ping
add dst-address=0.0.0.0/0 gateway=192.168.2.100 distance=2 check-gateway=ping
/ip firewall nat
add chain=srcnat out-interface=WAN1 action=masquerade
add chain=srcnat out-interface=WAN2 action=masquerade
*PCC WITH HOTSPOT (Reference)
/ip firewall nat add action=accept chain=pre-hotspot disabled=no dst-address-type=!local hotspot=auth
Wednesday, November 27, 2019
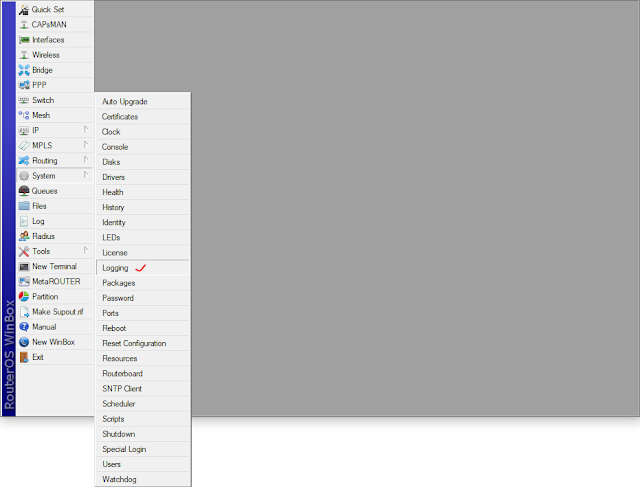
Limit to show log
We go to System > Logging > Actions > memory
By default is 1000. So we can set the number that we need.
By default is 1000. So we can set the number that we need.
Sunday, November 24, 2019
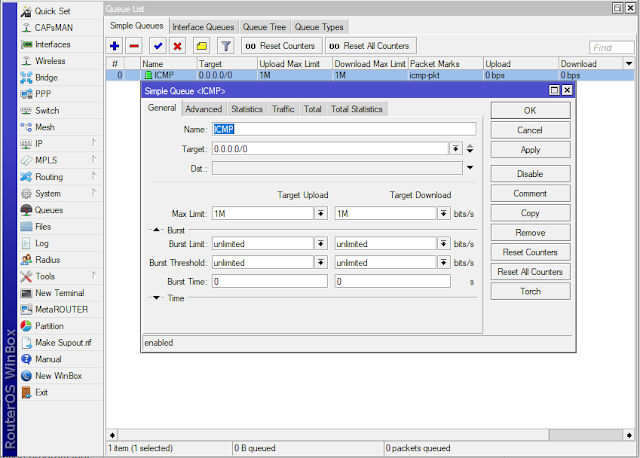
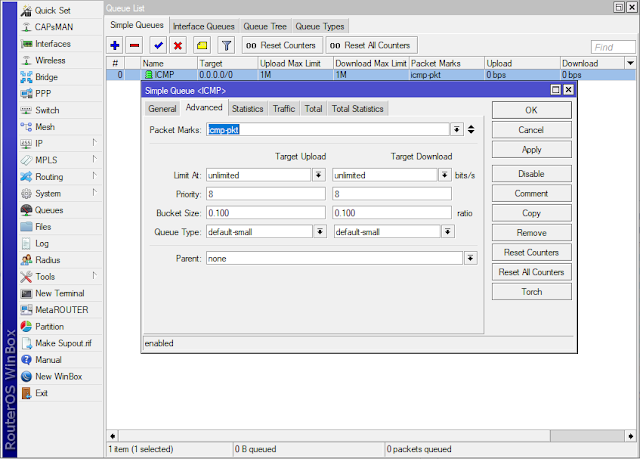
High Priortiy ICPM (Ping)
In this configuration we use MikroTik RouterBOARD wAP 2nD r2 with firmware 6.42.7
1. Create Mangle
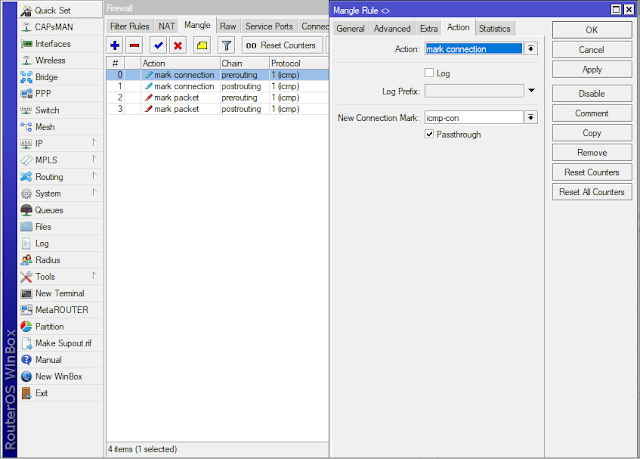
A. Create Mark Connection
/ip firewall mangle
add action=mark-connection chain=prerouting new-connection-mark=icmp-con passthrough=yes protocol=icmp
add action=mark-connection chain=postrouting new-connection-mark=icmp-con passthrough=yes protocol=icmp
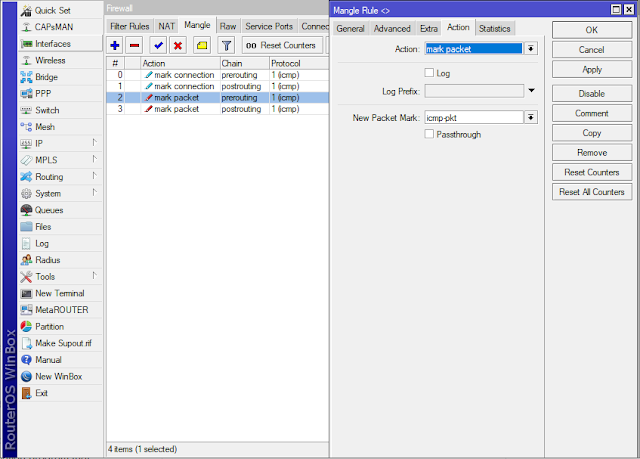
B. Create Mark Packet
/ip firewall mangle
add action=mark-packet chain=prerouting connection-mark=icmp-con new-packet-mark=icmp-pkt passthrough=no protocol=icmp
add action=mark-packet chain=postrouting connection-mark=icmp-con new-packet-mark=icmp-pkt passthrough=no protocol=icmp
2. Create Simple Queue
/queue simple
add max-limit=1M/1M name=ICMP packet-marks=icmp-pkt target="0.0.0.0/0"
1. Create Mangle
A. Create Mark Connection
/ip firewall mangle
add action=mark-connection chain=prerouting new-connection-mark=icmp-con passthrough=yes protocol=icmp
add action=mark-connection chain=postrouting new-connection-mark=icmp-con passthrough=yes protocol=icmp
B. Create Mark Packet
/ip firewall mangle
add action=mark-packet chain=prerouting connection-mark=icmp-con new-packet-mark=icmp-pkt passthrough=no protocol=icmp
add action=mark-packet chain=postrouting connection-mark=icmp-con new-packet-mark=icmp-pkt passthrough=no protocol=icmp
2. Create Simple Queue
/queue simple
add max-limit=1M/1M name=ICMP packet-marks=icmp-pkt target="0.0.0.0/0"
Monday, November 18, 2019
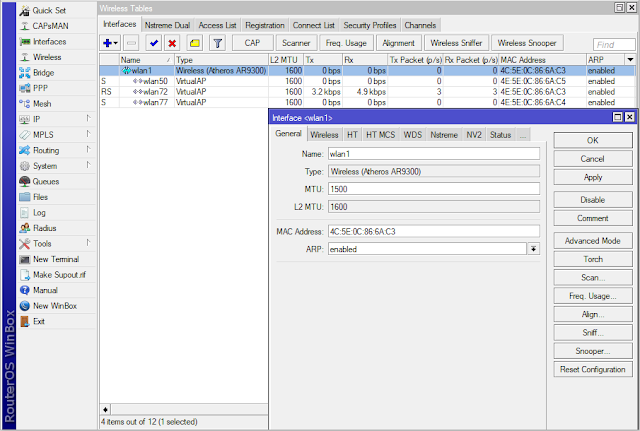
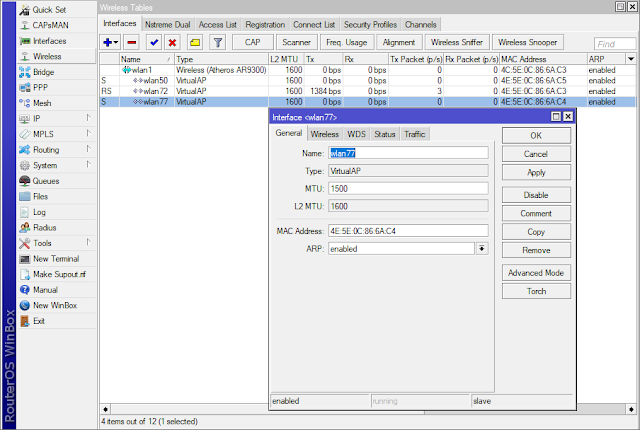
Multi SSID (VirtualAP) by using VLAN
1. Create Vlan
2. Configure Wireless Security Profiles
3. Configure Multi SSID with VirtualAP
4. Create Bridge and add Vlan and Wireless Interface to Bridge
5. Configure IP Address for Management Wifi
In this configuration we use MikroTik RBcAP2n with firmware 6.18. We configure this MikroTik for AP only and DHCP Server will provide from main Router.
Vlan 50: Guest user
Vlan 69: Management Wifi
Vlan 72: Staff
Vlan 77: Managment
1. Create Vlan
/interface vlan
add interface=ether1_TO-SW01:P10 name=vlan50 vlan-id=50
add interface=ether1_TO-SW01:P10 name=vlan69 vlan-id=69
add interface=ether1_TO-SW01:P10 name=vlan72 vlan-id=72
add interface=ether1_TO-SW01:P10 name=vlan77 vlan-id=77
2. Configure Wireless Security Profiles
/interface wireless security-profiles
add authentication-types=wpa-psk,wpa2-psk eap-methods="" management-protection=allowed mode=dynamic-keys name=bdc supplicant-identity="" wpa-pre-shared-key=BDC@5t@ff
wpa2-pre-shared-key=BDC@5t@ff
add authentication-types=wpa-psk,wpa2-psk eap-methods="" management-protection=allowed mode=dynamic-keys name=mgmt supplicant-identity="" wpa-pre-shared-key=@dm!n@MGMT
wpa2-pre-shared-key=@dm!n@MGMT
add authentication-types=wpa-psk,wpa2-psk eap-methods=""management-protection=allowed mode=dynamic-keys name=guest supplicant-identity="" wpa-pre-shared-key=5t@ff@GUEST
wpa2-pre-shared-key=5t@ff@GUEST
3. Configure Multi SSID with VirtualAP
/interface wireless
set [ find default-name=wlan1 ] band=2ghz-b/g/n disabled=no distance=indoors mode=ap-bridge ssid=""
/interface wireless
add disabled=no l2mtu=1600 mac-address=4E:5E:0C:86:6A:C5 master-interface=wlan1 name=wlan50 security-profile=guest ssid=BDC-GUEST wds-cost-range=0 wds-default-cost=0
add disabled=no l2mtu=1600 mac-address=4E:5E:0C:86:6A:C3 master-interface=wlan1 name=wlan72 security-profile=bdc ssid=BDC-STAFF wds-cost-range=0 wds-default-cost=0
add disabled=no l2mtu=1600 mac-address=4E:5E:0C:86:6A:C4 master-interface=wlan1 name=wlan77 security-profile=mgmt ssid=SIGROUP-MGMT wds-cost-range=0 wds-default-cost=0
4. Create Bridge and add Vlan and Wireless Interface to Bridge
/interface bridge
add name=bridge-vlan50
add name=bridge-vlan72
add name=bridge-vlan77
/interface bridge port
add bridge=bridge-vlan72 interface=vlan72
add bridge=bridge-vlan72 interface=wlan72
add bridge=bridge-vlan77 interface=vlan77
add bridge=bridge-vlan77 interface=wlan77
add bridge=bridge-vlan50 interface=vlan50
add bridge=bridge-vlan50 interface=wlan50
5. Configure IP Address for Management Wifi
/ip address
add address=172.16.69.200/24 interface=vlan69 network=172.16.69.0
/ip route
add distance=1 gateway=172.16.69.1
2. Configure Wireless Security Profiles
3. Configure Multi SSID with VirtualAP
4. Create Bridge and add Vlan and Wireless Interface to Bridge
5. Configure IP Address for Management Wifi
In this configuration we use MikroTik RBcAP2n with firmware 6.18. We configure this MikroTik for AP only and DHCP Server will provide from main Router.
Vlan 50: Guest user
Vlan 69: Management Wifi
Vlan 72: Staff
Vlan 77: Managment
1. Create Vlan
/interface vlan
add interface=ether1_TO-SW01:P10 name=vlan50 vlan-id=50
add interface=ether1_TO-SW01:P10 name=vlan69 vlan-id=69
add interface=ether1_TO-SW01:P10 name=vlan72 vlan-id=72
add interface=ether1_TO-SW01:P10 name=vlan77 vlan-id=77
2. Configure Wireless Security Profiles
/interface wireless security-profiles
add authentication-types=wpa-psk,wpa2-psk eap-methods="" management-protection=allowed mode=dynamic-keys name=bdc supplicant-identity="" wpa-pre-shared-key=BDC@5t@ff
wpa2-pre-shared-key=BDC@5t@ff
add authentication-types=wpa-psk,wpa2-psk eap-methods="" management-protection=allowed mode=dynamic-keys name=mgmt supplicant-identity="" wpa-pre-shared-key=@dm!n@MGMT
wpa2-pre-shared-key=@dm!n@MGMT
add authentication-types=wpa-psk,wpa2-psk eap-methods=""management-protection=allowed mode=dynamic-keys name=guest supplicant-identity="" wpa-pre-shared-key=5t@ff@GUEST
wpa2-pre-shared-key=5t@ff@GUEST
3. Configure Multi SSID with VirtualAP
/interface wireless
set [ find default-name=wlan1 ] band=2ghz-b/g/n disabled=no distance=indoors mode=ap-bridge ssid=""
/interface wireless
add disabled=no l2mtu=1600 mac-address=4E:5E:0C:86:6A:C5 master-interface=wlan1 name=wlan50 security-profile=guest ssid=BDC-GUEST wds-cost-range=0 wds-default-cost=0
add disabled=no l2mtu=1600 mac-address=4E:5E:0C:86:6A:C3 master-interface=wlan1 name=wlan72 security-profile=bdc ssid=BDC-STAFF wds-cost-range=0 wds-default-cost=0
add disabled=no l2mtu=1600 mac-address=4E:5E:0C:86:6A:C4 master-interface=wlan1 name=wlan77 security-profile=mgmt ssid=SIGROUP-MGMT wds-cost-range=0 wds-default-cost=0
4. Create Bridge and add Vlan and Wireless Interface to Bridge
/interface bridge
add name=bridge-vlan50
add name=bridge-vlan72
add name=bridge-vlan77
add bridge=bridge-vlan72 interface=vlan72
add bridge=bridge-vlan72 interface=wlan72
add bridge=bridge-vlan77 interface=vlan77
add bridge=bridge-vlan77 interface=wlan77
add bridge=bridge-vlan50 interface=vlan50
add bridge=bridge-vlan50 interface=wlan50
/ip address
add address=172.16.69.200/24 interface=vlan69 network=172.16.69.0
/ip route
add distance=1 gateway=172.16.69.1
Subscribe to:
Comments (Atom)